i'm using pam along with google authenticator to access my servers. but i didn't knew how to exclude some users from pam. when i finally solved the problem, i couldn't find this exact issue on google. so, this blog post is a quick guide to show how to create test users outside of pam. all this work for is just tunneling, but you might get some different ideas by reading this. first, create test user with a strong password, and using --shell /usr/bin/false flag. alternatively, /etc/passwd entry of test user can be edited to assign /usr/bin/false, instead /bin/bash.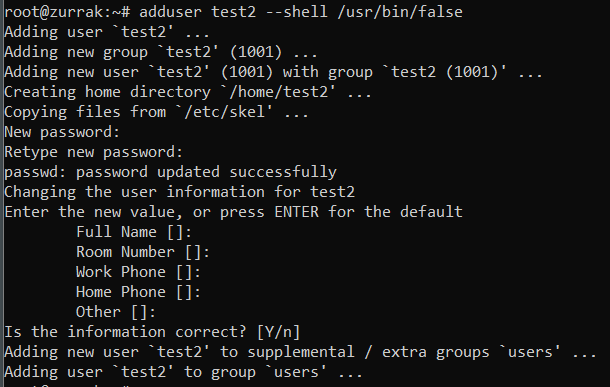 ♦edit /etc/pam.d/sshd with your favorite editor. add auth [success=1 default=ignore] pam_succeed_if.so user = test2 line at the top. (as you can see, my test user is "test"). don't forget to add a comment line what that line does.
♦edit /etc/pam.d/sshd with your favorite editor. add auth [success=1 default=ignore] pam_succeed_if.so user = test2 line at the top. (as you can see, my test user is "test"). don't forget to add a comment line what that line does.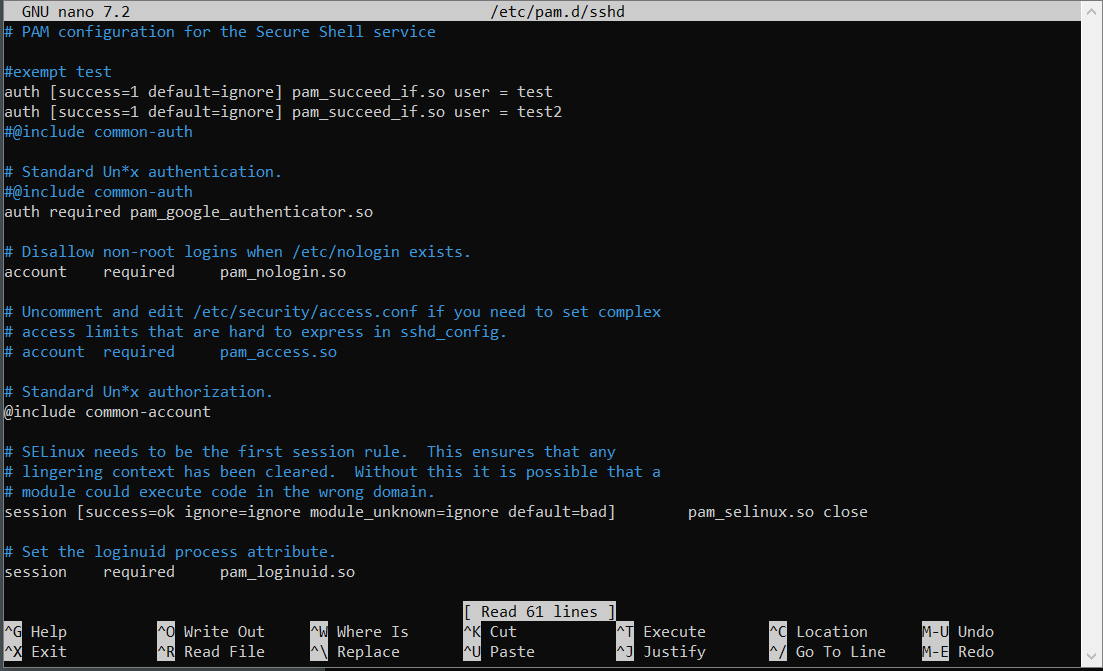 ♦edit /etc/ssh/sshd_config with your favorite editor. add this block to bottom: Match User test,test2 ChallengeResponseAuthentication no PasswordAuthentication yes AuthenticationMethods password publickey ForceCommand /bin/false
♦edit /etc/ssh/sshd_config with your favorite editor. add this block to bottom: Match User test,test2 ChallengeResponseAuthentication no PasswordAuthentication yes AuthenticationMethods password publickey ForceCommand /bin/false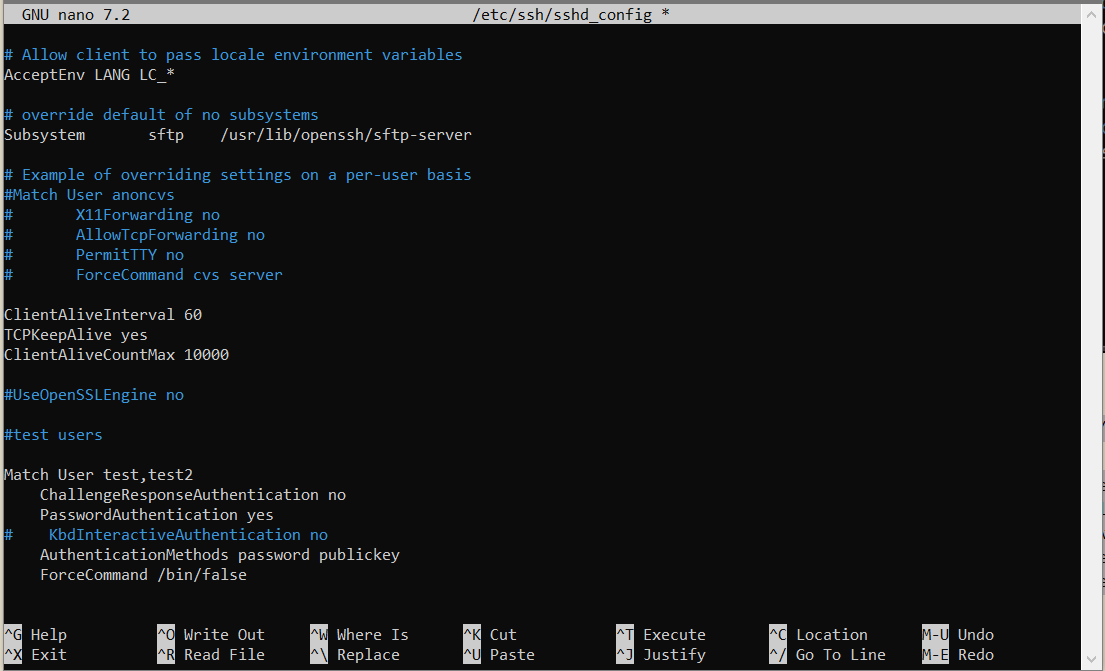 ♦as you can see, i added /bin/false again by ForceCommand, just to be sure. also, authorized_keys command option can be considered. now, ssh won't ask for a verification code. let's create ssh keys. again, strong password.
♦as you can see, i added /bin/false again by ForceCommand, just to be sure. also, authorized_keys command option can be considered. now, ssh won't ask for a verification code. let's create ssh keys. again, strong password.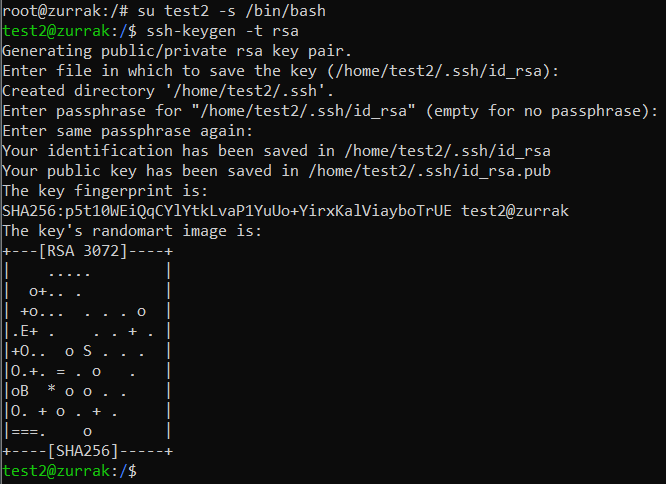 ♦when trying to ssh, it won't work normally because i've disabled password login for security. i recommend everyone to configure key with passphrase.
♦when trying to ssh, it won't work normally because i've disabled password login for security. i recommend everyone to configure key with passphrase.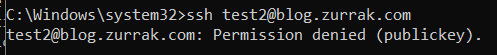 ♦since we assigned /bin/false twice in server, connection with shell is not possible. so we're just going to tunnel with -D and -N flags. it won't output something, but the connection is made.
♦since we assigned /bin/false twice in server, connection with shell is not possible. so we're just going to tunnel with -D and -N flags. it won't output something, but the connection is made.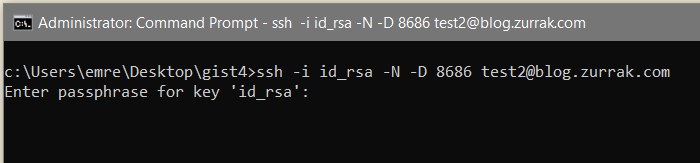 ♦after configuring foxyproxy, the connection was successful.
♦after configuring foxyproxy, the connection was successful.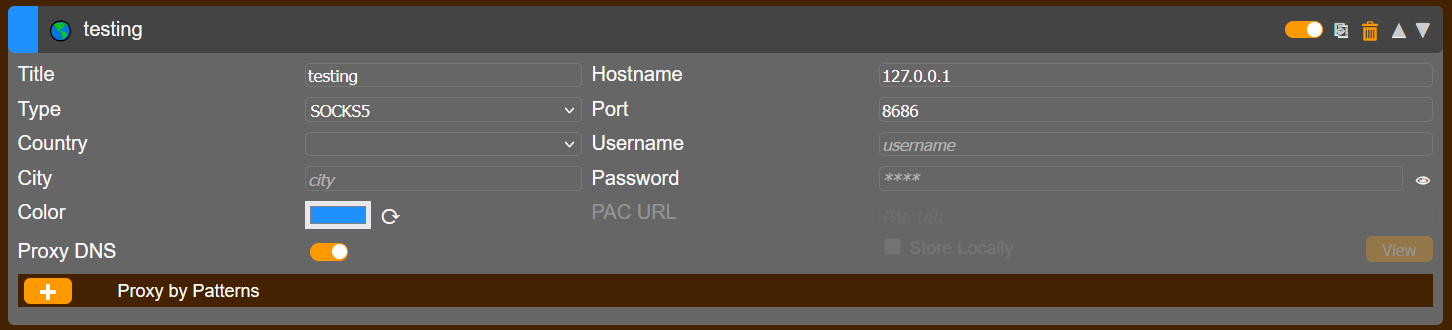
let's roll!
if you have questions: contact
